Open-source software (OSS) is more than just a development convenience — it’s the critical foundation of modern digital infrastructure. By 2026, open-source security will be a central concern for businesses, not only for innovation but for trust, risk management, and compliance.
In this blog, we analyze where open-source security is heading, why DevSecOps is becoming a non-negotiable discipline, and how SBOM (Software Bill of Materials) requirements are evolving — especially for U.S.-based companies. Whether you’re a CTO, a developer, or a business leader, this insight will help you prepare for the future.
Why Open Source Security Is a Top Priority in 2026
As businesses increasingly rely on open-source software, ensuring its security has never been more critical. Vulnerabilities in third-party components can pose serious risks, from data breaches to compliance issues. Understanding why open-source security is a top priority in 2026 helps organizations prepare and implement effective strategies.
1. Explosive Use of OSS + Rising Threat Surface
- – Modern applications rely heavily on open-source components. According to online research, a large percentage of software today is built upon open-source libraries.
- – However, increased use means more exposure: malicious packages, supply chain attacks, and dependency confusion are very real risks.
- – Attack vectors are evolving: software supply chain attacks (like typosquatting) are now common attack methods.
2. Regulatory & Compliance Pressure
- – The growing regulatory landscape means that companies not preparing now could struggle to comply in the near future.
- – U.S. Executive Order 14028 mandates SBOMs for software sold to or used by federal agencies.
- – Many businesses (even outside the public sector) are preemptively adopting SBOM practices to meet client or partner demands.
DevSecOps: The New Standard for Open-Source Development
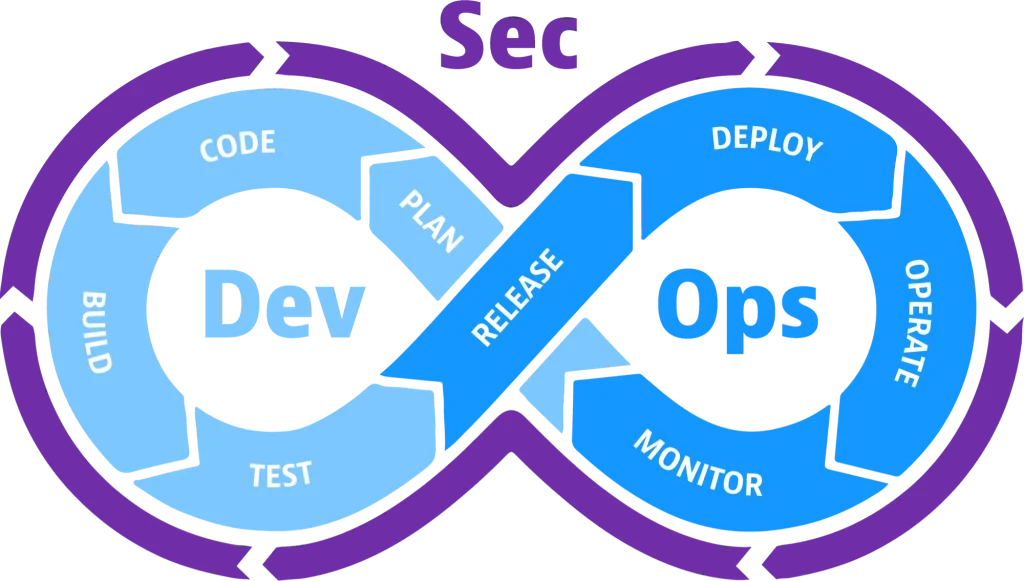
What Is “Open Source DevSecOps”?
DevSecOps is the practice of integrating security into every stage of the development lifecycle — from planning and coding to testing, deployment, and monitoring. For open-source projects, this means:
- – Automatically scanning dependencies
- – Securing infrastructure as code
- – Shifting security “left” so vulnerabilities are caught early
Why DevSecOps Matters More Than Ever in 2026
-
Shift-Left Security
- – Security is no longer just a gate before production: it’s embedded in the CI/CD pipeline.
- – Developers get feedback early (via static analysis, SAST, SCA), reducing expensive rework.
-
AI and Automation
- – AI-driven security tools are increasingly common. These tools can detect, prioritize, and even fix vulnerabilities without human intervention.
- – Continuous compliance checks become automated — reducing manual effort and error.
-
Regulatory Integration & Compliance as Code
- – Security-as-Code: embedding compliance rules, security policies, and threat models directly into code.
- – This helps teams satisfy regulatory requirements (like SBOM generation) within their DevSecOps processes.
-
Secure Development Culture
- – A DevSecOps mindset encourages shared responsibility: developers, operations, and security teams collaboratively manage risk.
- – For open-source projects, this also strengthens trust: contributors and users can validate the security posture of the software.
SBOM Requirements: The Backbone of Transparency
What Is SBOM?
A Software Bill of Materials (SBOM) is essentially a detailed inventory of all components, dependencies, libraries, and versions used in a piece of software.
Why SBOMs Are Critical in 2026
- – Regulatory Demand: As noted, U.S. Executive Order 14028 requires SBOMs for certain types of software.
- – Security Insight: SBOMs allow teams to quickly identify vulnerable or outdated components.
- – Supply Chain Governance: By having a “bill of materials,” companies can better manage software supply chain risk.
- – Continuous Compliance: SBOMs should be updated with every new release to remain effective.
Best Practices for SBOM Adoption
- – Use automated tools to generate SBOMs in standard formats (e.g., SPDX, CycloneDX).
- – Integrate SBOM generation into DevSecOps pipelines.
- – Regularly scan your SBOM against vulnerability databases.
- – Maintain a versioned SBOM for each release.
- – Provide SBOMs to your customers or partners when requested — especially if you serve regulated customers.
Emerging Trends & Predictions for 2026

Here’s what’s likely to shape open-source security, DevSecOps, and SBOM practices in the next few years:
-
Market Growth
- – The DevSecOps market is expected to accelerate rapidly, fueled by SBOM requirements and the growing cost of supply chain risk.
-
Security Tools Innovation
- – We’ll see more open-source and AI-powered security tools tailored for open-source ecosystems.
- – Tools like SCA scanners, code-signing (e.g., Sigstore), and policy-as-code will become more mature.
-
Build Reproducibility & Transparency
- – New research shows a push toward reproducible builds — meaning binaries can be rebuilt identically from source.
- – This will help validate SBOM authenticity and reduce risk from tampered artifacts.
-
Stronger Supply-Chain Standards
- – Academic and industry work on supply chain “smells” — suspicious dependency structures, outdated or risky sub-dependencies — will drive tool development.
- – Standardisation efforts (e.g., SLSA – Supply-chain Levels for Software Artifacts) will gain broader adoption.
What Should CTOs, Developers & Business Leaders Do Now?
Here’s a practical roadmap for adopting open-source security best practices by 2026:
-
Audit Your Open Source Usage
- Inventory all open-source dependencies in your stack.
- Generate an SBOM for your current version and start embedding this into your release process.
-
Embed DevSecOps
- Integrate static (SAST) and dependency (SCA) scanning in your CI/CD pipelines. Tools like GitLab Ultimate or open-source equivalents help.
- Adopt a shift-left security culture: train developers, enforce security-as-code policies, and include compliance checks early.
-
Automate SBOM Generation
- Use tools that support standard SBOM formats.
- Make SBOM generation part of your build pipeline to ensure it’s always up to date.
-
Monitor & Respond
- Continuously scan your SBOM against vulnerability databases.
- Use AI-driven alerting or analysis to prioritize and remediate critical issues quickly.
-
Govern for Compliance
- Develop policy-as-code so that security, DevSecOps, and SBOM compliance are baked into your processes.
- Document your SBOM, threat model, and security policies — this will help in audits and customer trust.
Why This Matters for Business & Product Owners
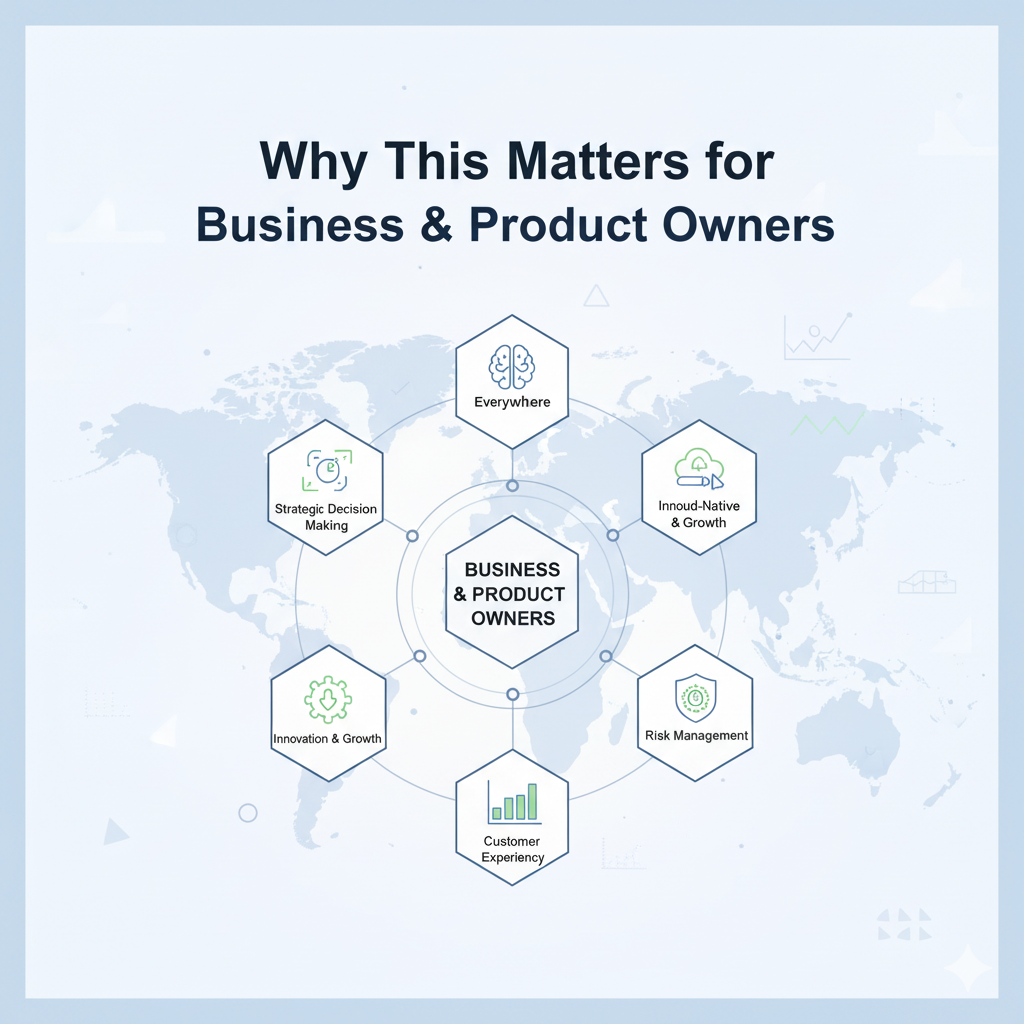
- – Risk Mitigation: By proactively addressing OSS risk, you reduce the chance of supply chain attacks, which are becoming more frequent.
- – Trust & Differentiation: Firms that provide SBOMs and commit to DevSecOps can differentiate themselves as more trustworthy and secure.
- – Regulatory Readiness: For companies working with U.S. government entities or large enterprises, SBOM readiness will become a requirement, not an option.
- – Efficiency: DevSecOps and automation improve developer productivity, by catching issues earlier and reducing manual security work.
Final Thoughts
The landscape of open-source software in 2026 will be radically more security-conscious than it is today. DevSecOps, once a niche discipline, is becoming central. SBOM, once optional, is now a compliance requirement in many contexts. Businesses that take proactive steps now to operationalize secure open-source development won’t just survive — they’ll gain a competitive edge.
If you’re leading a development team or building a product that uses open-source components, it’s time to act: build your SBOM strategy, integrate DevSecOps deeply, and embrace transparency. The future favors those who combine innovation with responsibility.
Frequently Asked Questions (FAQ) :
1. What is open source security in 2026?
Open source security in 2026 means proactively managing vulnerabilities, compliance, and supply chain risks in all software projects using open code.
2. Why is DevSecOps important for open source software?
DevSecOps integrates security checks throughout the development process, making it easier to detect and fix issues early in open source projects.
3. What is an SBOM?
An SBOM (Software Bill of Materials) is a detailed list of all software components and dependencies used in a project.
4. Why are US companies facing stricter SBOM policies in 2026?
Due to new regulations and increased cyber threats, US companies must now provide SBOMs to prove software transparency and reduce risk.
5. How can DevSecOps improve open source development?
By automating security testing, code reviews, and dependency management during DevOps workflows.
6. How do you create an SBOM for your project?
You can use tools like CycloneDX or SPDX to automatically generate SBOMs as part of your CI/CD pipeline.
7. What are common security risks in open source software?
Outdated dependencies, unpatched vulnerabilities, misconfigurations, and lack of visibility into third-party code.
8. What’s a best practice for managing open source dependencies?
Regularly audit, update, and remove unused packages to lower the attack surface.
9. What tools support open source DevSecOps?
Popular tools include Snyk, Mend, OWASP Dependency-Check, and GitHub Advanced Security.
10. Are there regulations requiring SBOMs in the US?
Yes, new federal requirements and executive orders mandate SBOMs for software sold to government agencies.

![Why Are People Leaving SuiteCRM? [2025 Insights & Alternatives] Why Are People Leaving SuiteCRM? [Insights & Alternatives]](https://devdiligent.com/blog/wp-content/uploads/2025/10/Untitled-design-10.png)